IPSec site-to-site configuration guide with Palo Alto
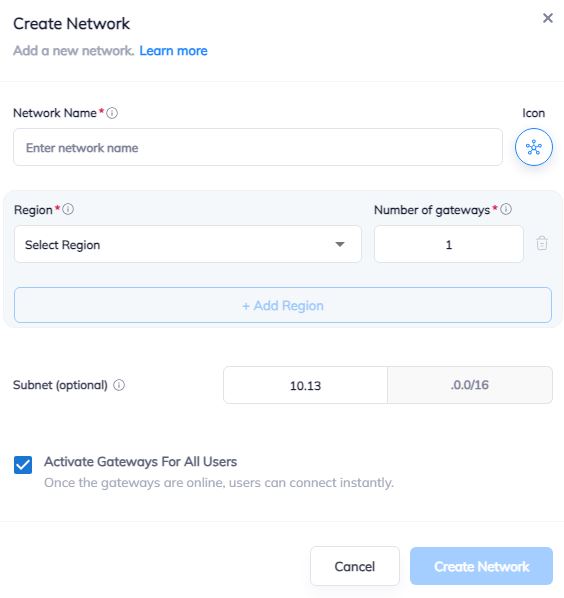
1. Login to vipilink portal and create network
1.1 Go to Networks section and create a new network.
1.2 Define the network name.
1.3 Select the region and gateways number.
1.4 Choose the subnet.
1.5 Activate gateways for all users section is active by default. If you want to disable this function - just remove the mark.
2. Create the IPsec tunnel in the Vipilink portal
2.1 Go to Networks section and click on the subnet that you created in Step-1.
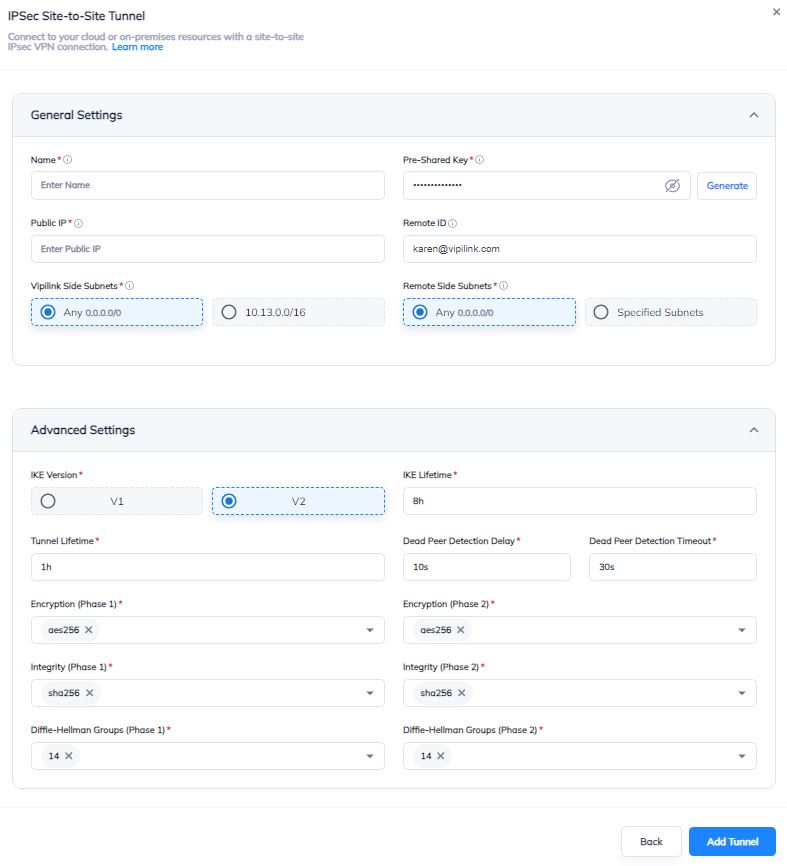
2.2 Click on Gateway and add a Tunnel. Choose IPSec Site-to-Site Tunnel and press to continue.
2.3 Choose between a Single-Tunnel and Dual-Tunnel.
2.4 General Settings Values
-
Name
-
Public IP
-
Vipilink Side Subnets
-
Pre-Shared Key
-
Remote ID
-
Remote Side Subnets
2.5 Advanced Settings Values
-
Ike Version
-
Tunnel Lifetime
-
Encryption (Phase 1)
-
Integrity (Phase 1)
-
Diffie-Helman Groups (Phase 1)
-
Ike Lifetime
-
Dead Peer Detection Delay
-
Dead Peer Detection Timeout
-
Encryption (Phase 2)
-
Integrity (Phase 2)
-
Diffie-Helman Groups (Phase 2)
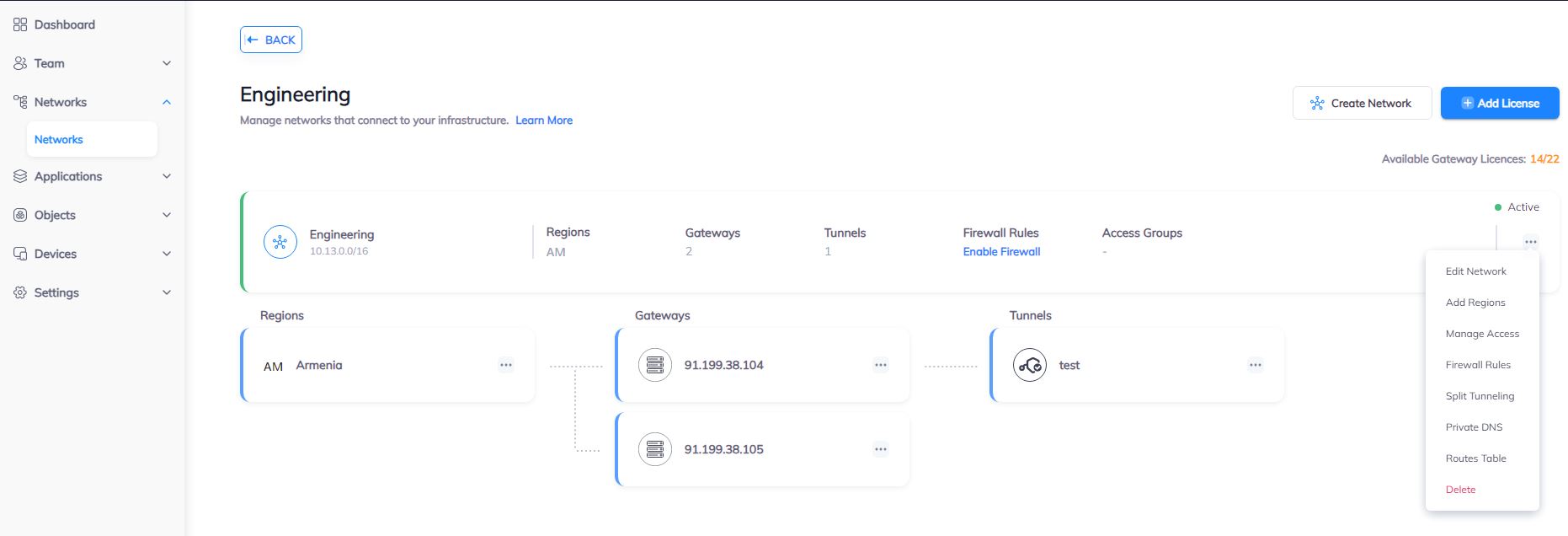
2.6 You can also manage a Network, Regions, Access, Firewall Rules, Routes Table, enable Split Tunneling and Private DNS.
3. Create the IPsec tunnel on Palo Alto
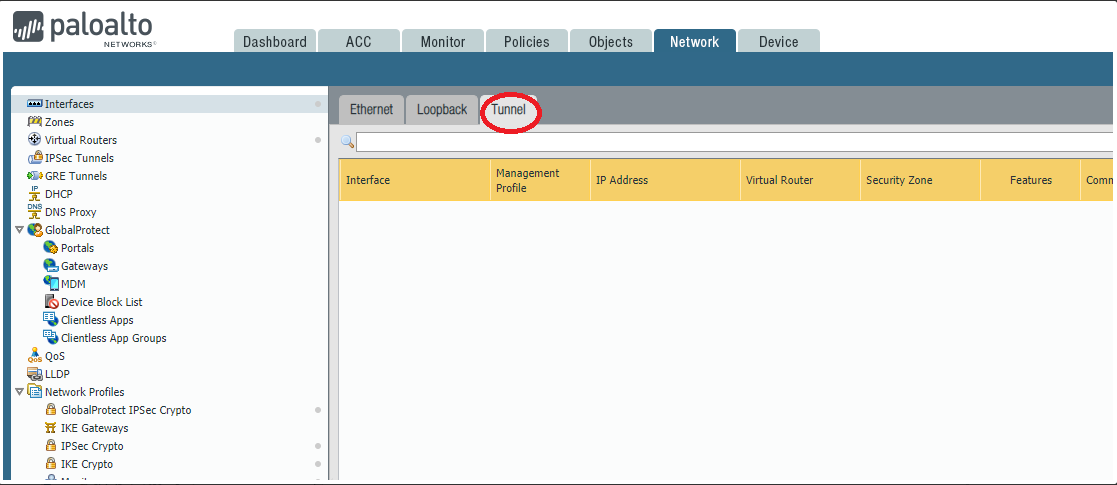
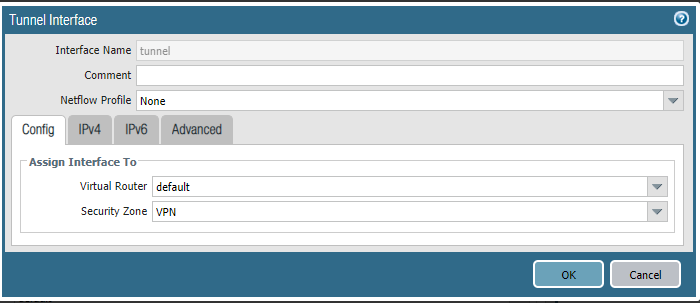
3.1 Log in to Palo Alto Web Interface and go Network/Interfaces/Tunnel and add a new tunnel.
3.2 In Config/Assign Interface To section select the Virtual Router you want tunnel interface be in.
3.3 In the same section configure new zone for the tunnel interface. If incoming or outgoing traffic is in other zone than tunnel interface is, you have to add a policy to allow traffic flow.
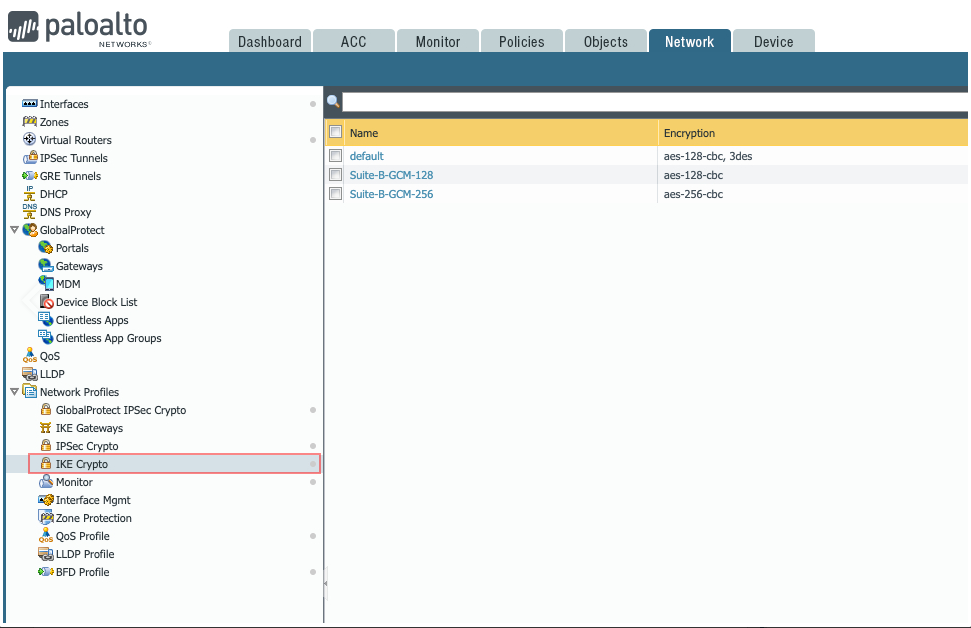
3.4 Open Network Profiles/IKE Crypto and add a new profile with Phase 1 parameters.
-
Name - Define the name
-
DH Group - group14
-
Encryption - aes-256-cbc
-
Authentication - sha256
-
Key Lifetime - 8 Hours
-
IKEv2 Authentication Multiple - 0
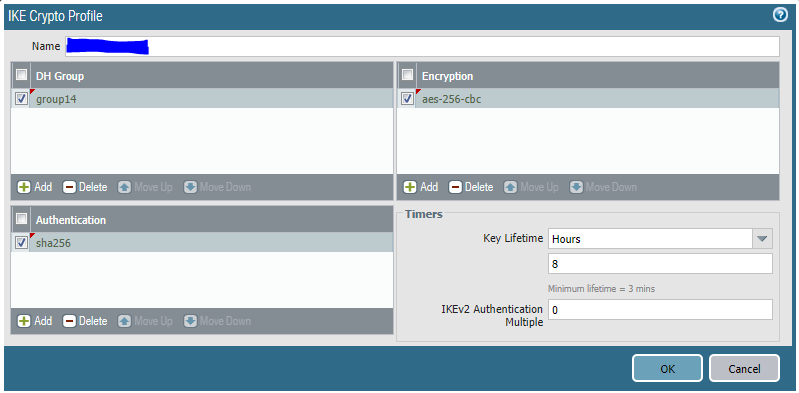
3.5 Go to Network/Network Profiles/IKE Gateway and add a new gateway.
-
Name - Define the name
-
Version - IKEv2 only mode
-
Address Type - IPv4
-
Interface - WAN
-
Local IP Address - WAN IP Address
-
Peer IP Address Type - IP
-
Peer Address - Vipilink Gateway IP Address
-
Authentication - Pre-shared Key
-
Pre-shared Key - define your PSK
-
Confirm Pre-shared Key - retype your PSK
-
Local Identification - none
-
Peer Identification - none
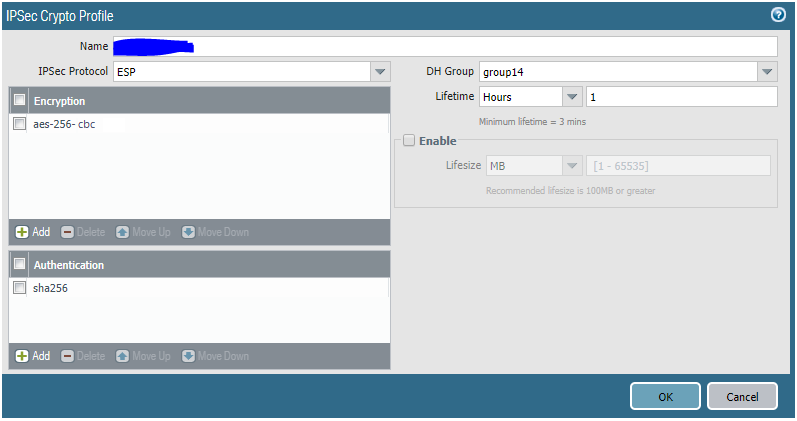
3.6 Go to Network/Network Profiles/IPSec Crypto and add a new profile.
-
Name - Define the name
-
IPSec Protocol - ESP
-
DH Group - group14
-
Encryption - aes-256-cbc
-
Authentication - sha256
-
Lifetime - 1 Hours
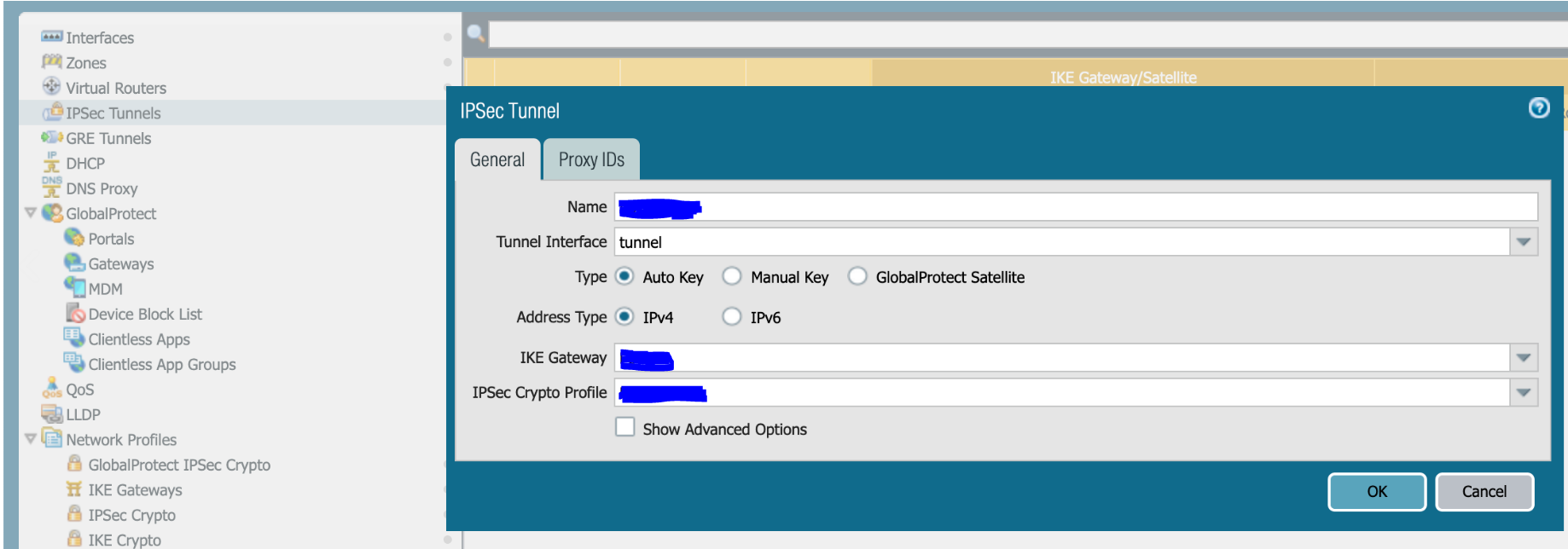
3.7 Go to Network/IPSec Tunnels and add a new tunnel.
-
Name - Define the name
-
Tunnel Interface - tunnel
-
Type - Auto Key
-
Address Type - IPv4
-
IKE Gateway - select the gateway created in step 3.5
-
IPSec Crypto Profile - select the profile created in step 3.6
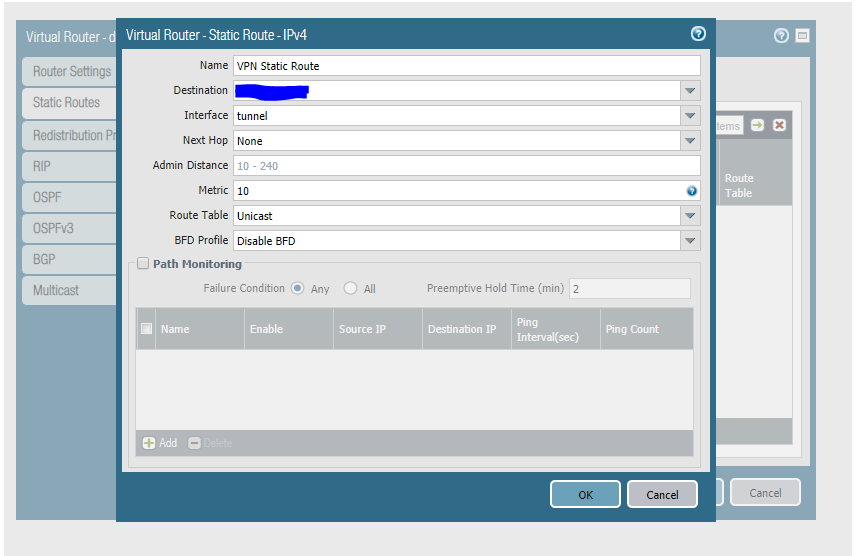
4.1 Go to Network/Virtual Routers/Static Routes and add a new route.
-
Name - Define the name
-
Destination - Vipilink Subnet
-
Interface - tunnel
-
Next Hope - None
-
Metric - 10
-
Route Table - Unicast
-
BFD Profile - Disable BFD
5.1 Go to Policies/Security. By default traffic will be allowed.

5.2 Test connectivity.